KATHMANDU: Cyber-enabled frauds (CEF) are becoming a major concern in Nepal. An analysis of Suspicious Transaction Reports (STRs), Suspicious Activity Reports (SARs), and Threshold Transaction Reports (TTRs) show a sharp increase in fraud-related activities, according to a Strategic Analysis Report on Cyber-enabled Frauds launched by the Nepal Rastra Bank on Sunday.
According to the report prepared by the Financial Information Unit (FIU) of Nepal Rastra Bank, around 15% of the STR/SARs received in 2024 (till May 31) were related to predicate offense ‘fraud’, with over 63% of these linked to cyber-enabled frauds. Most fraud-related STRs and SARs were forwarded to the Nepal Police and the Central Investigation Bureau (CIB), followed by the Department of Revenue Investigation (DRI) and the Department of Money Laundering Investigation (DMLI). While commercial and development banks reported the majority of CEF cases, reports from payment service providers (PSPs), despite the frequent use of digital wallets for such fraud, remain surprisingly low, according to the report.
As per Section 10 (A) of the Assets (Money) Laundering Prevention Act, 2008, the unit is required to submit an annual report through Nepal Rastra Bank to the government, detailing types of money laundering and terrorist financing offenses, including methods, techniques, and trends.
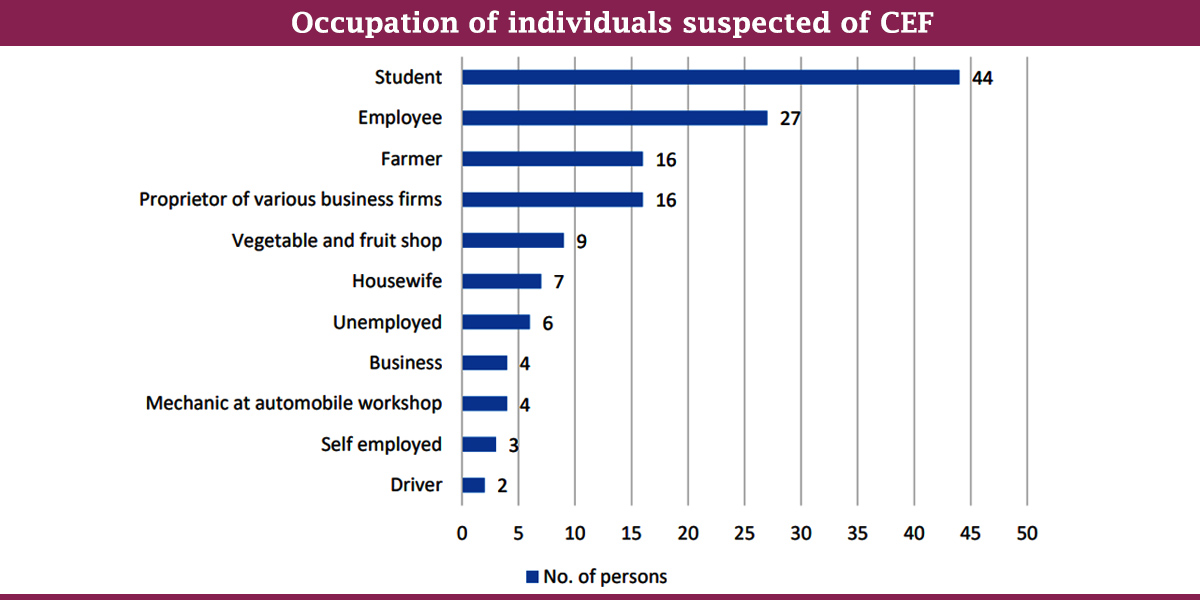
The report shows that individuals aged 19–30 are predominantly linked to CEF cases. This age group comprised 70% of suspects. Those in the 19–24 age group account for the largest share, often acting directly or as money mules. Many accounts linked to fraud were associated with students, employees, and small-scale entrepreneurs like vegetable sellers.
The analysis revealed that nearly half of fraudulent accounts were reported within three months of being opened, with three-fourths flagged within nine months. This suggests a preference for new accounts to launder fraud proceeds. Fraudsters often use the same credentials and mobile numbers to open multiple accounts across banks and PSPs, exploiting systemic loopholes.
 cyer
cyer
According to the report, the main trigger for CEF-related STR/SARs generation from reporting entities (REs) was reporting by the victim to REs. Inquiry from law enforcement and investigative agencies was another significant reason for STR/SARs reporting. Similarly, transactions monitoring by BFIs and PSOs, adverse news,
walk-in customers and letter from regulators like Nepal Rastra Bank were other factors contributing for the initiation of STR/SARs.
Bagmati Province reported the highest number of accounts linked to CEF, followed by Madhesh and Koshi provinces. Fraudsters are found to have withdrawn funds using ATMs across Nepal and India or transfer them to other bank and wallet accounts. Many accounts showed frequent small transactions, sometimes as low as Re. 1, credited to multiple wallet accounts linked to common mobile numbers, according to the report.
Fraudsters are found to have employed various techniques, including gift/parcel scams, social media impersonation, fake online businesses, lottery fraud and cryptocurrency investment schemes. Other methods involved false advertisements for online room rentals and examination fees for PTE and IELTS. Victims are typically contacted via social media, with fraudsters using evolving tactics to avoid detection, the report added.
The central bank has recommended strengthening Know-Your-Customer (KYC) processes by incorporating biometric verification and ensuring mobile numbers linked to accounts are registered in the customer’s or a family member’s name to control CEF. It has said that multi-factor authentication methods, such as OTPs, biometric verification, and authenticator apps, should be adopted for verifying high-value transactions and when new devices are added to accounts. Similarly, it has suggested limiting transaction volume and device access for newly opened accounts during an initial cooling-off period. It has also called for the implementation of advanced, real-time transaction monitoring systems to detect unusual activity based on patterns such as transaction value, frequency, geolocation and device usage.

 Himal Press
Himal Press